Overview - Features - Full Stack
Since the key feature of Blinky-Lite is remote access, security is the driving force in the development of Blinky-Lite. To be secure, a control platform must be complete or full-stack. Most available control platforms are just communication protocols. This leaves the user with missing functionality which often leads to a patchwork system, riddled with potential security vulnerabilities.
In contrast, Blinky-Lite strives to deliver a complete system. Not only does Blinky-Lite provide a set of device interfaces, a communication protocol, and configuration databases, it also provides
- an alarm system,
- notification system,
- device viewers,
- and plotting packages.
The data archiving system also includes access and setting history. User authentication interfaces include one-time-password, two factor authentication. And, instead of name-value pairs, device data is object-oriented which lends to complex data types, such as vectors and images. There is even an integrated logbook application, with hooks into the notification system.
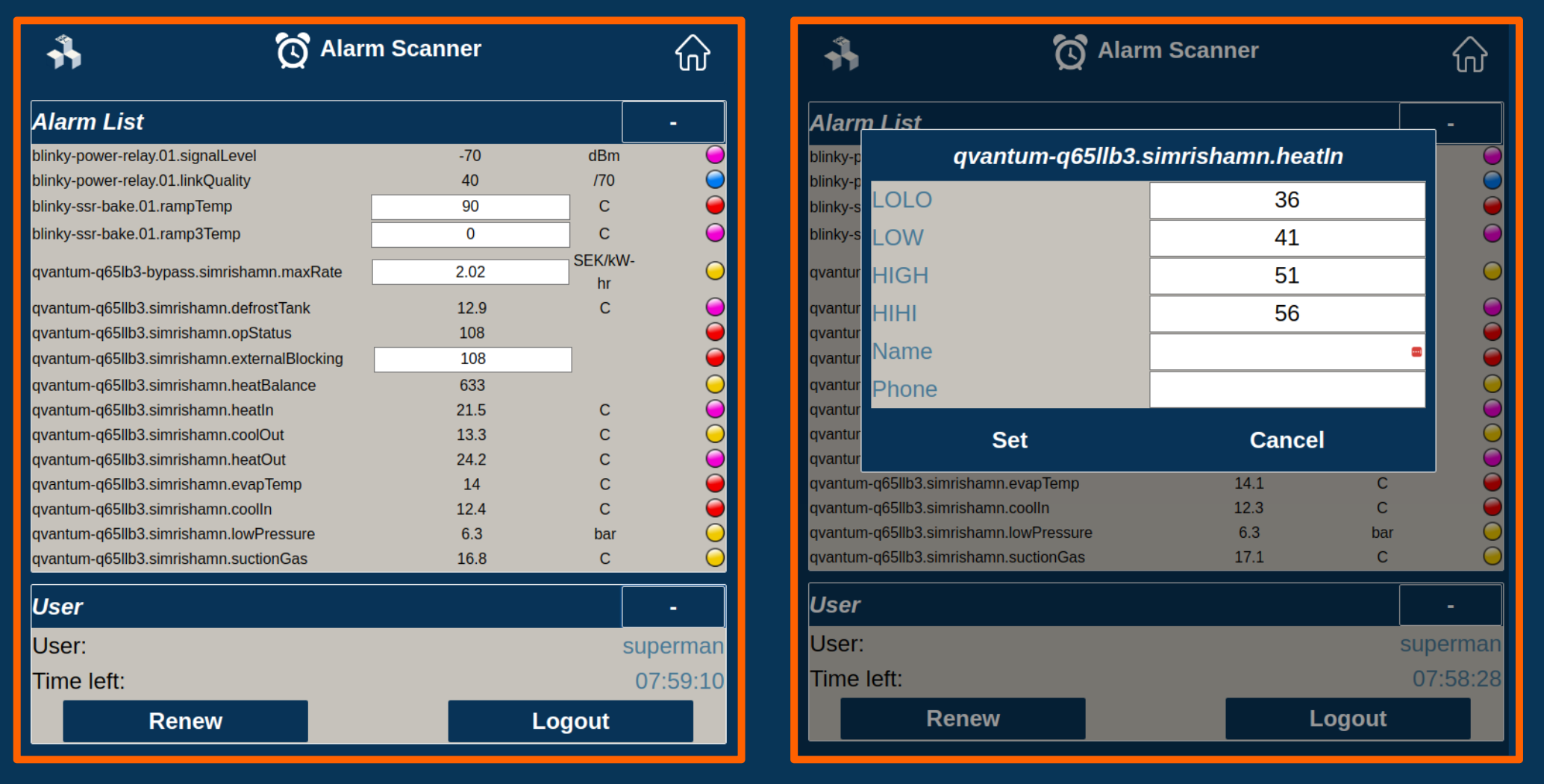
Blinky-Lite Alarm Scanner
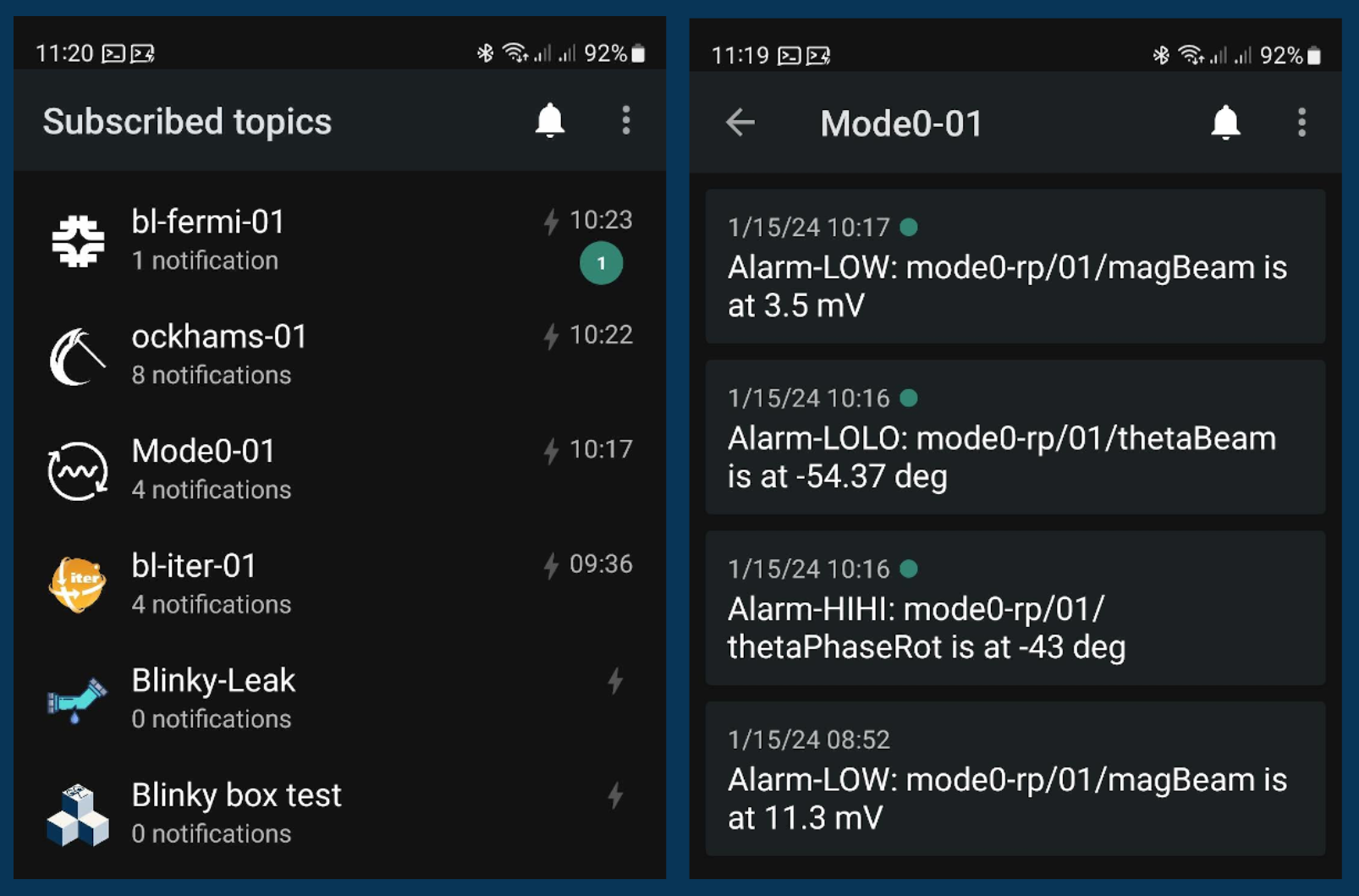
Blinky-Lite Notification Application
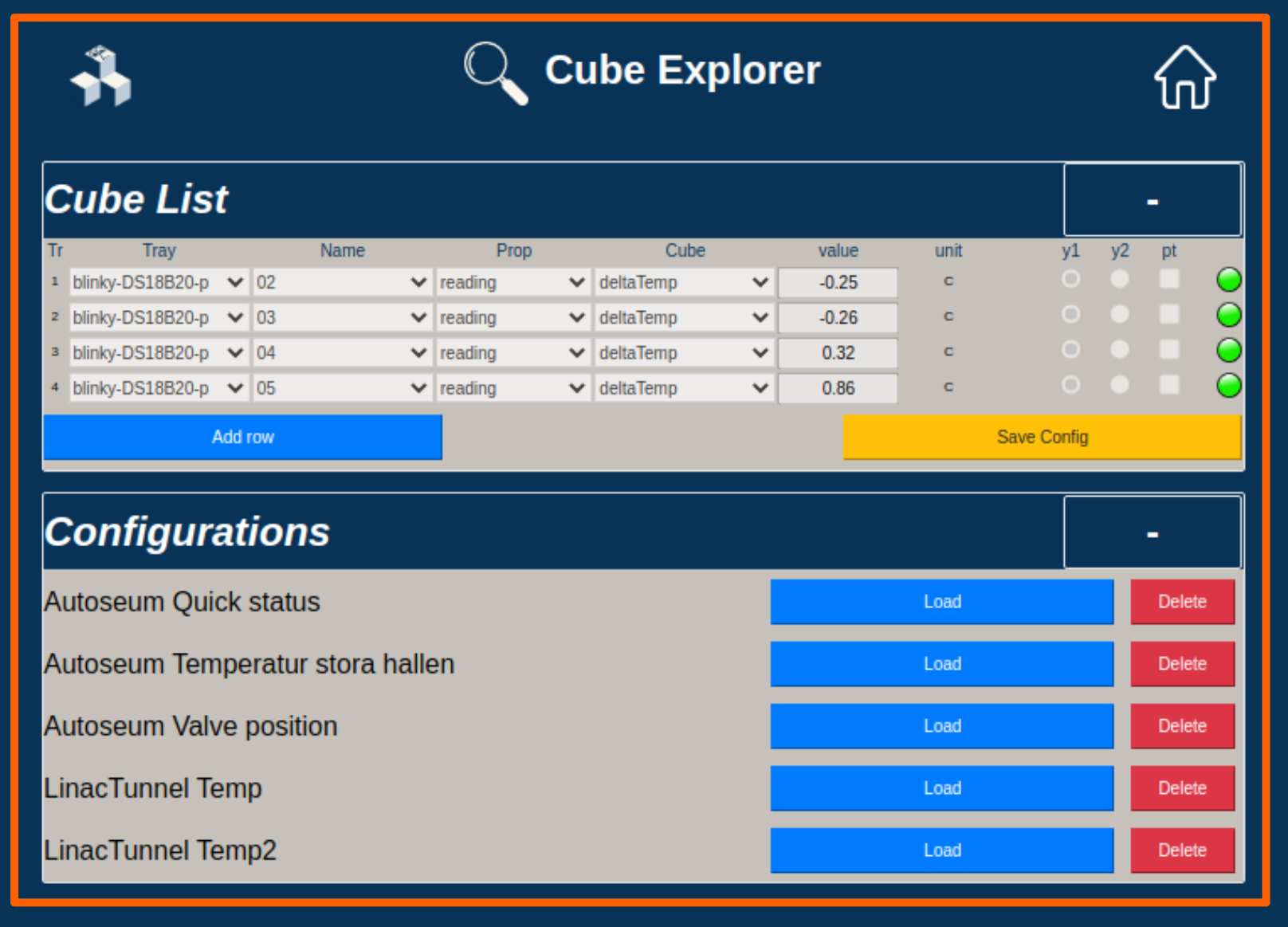
Blinky-Lite Device Viewer
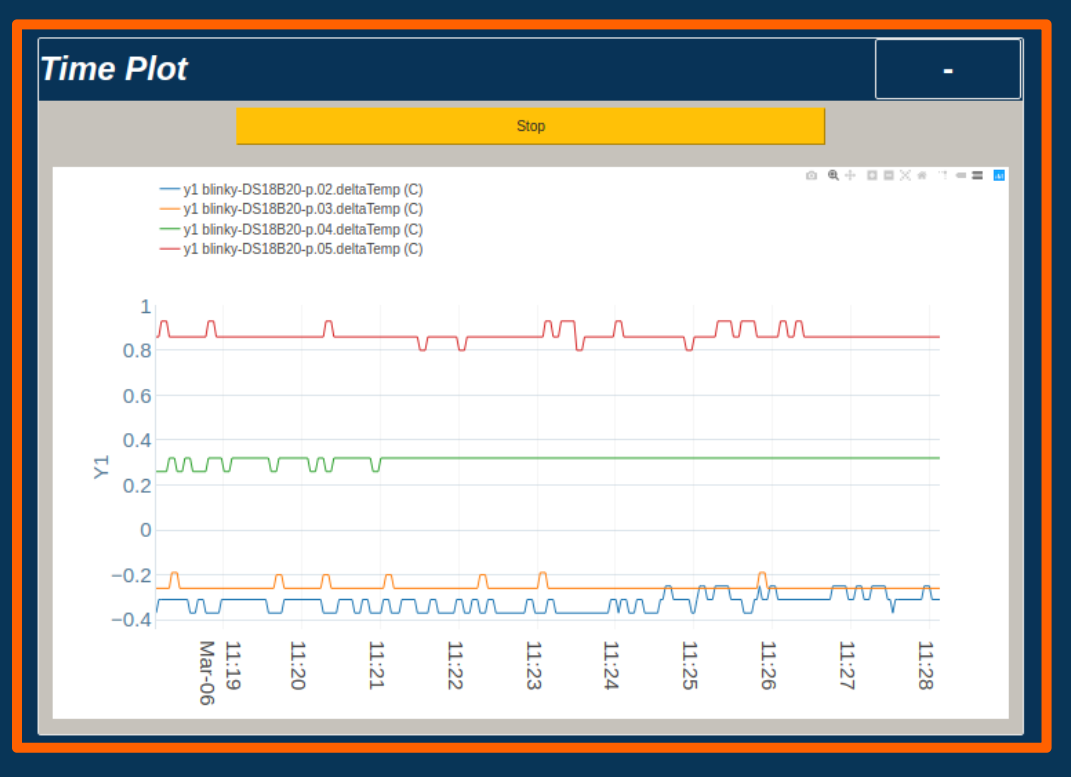
Blinky-Lite Time Plotter
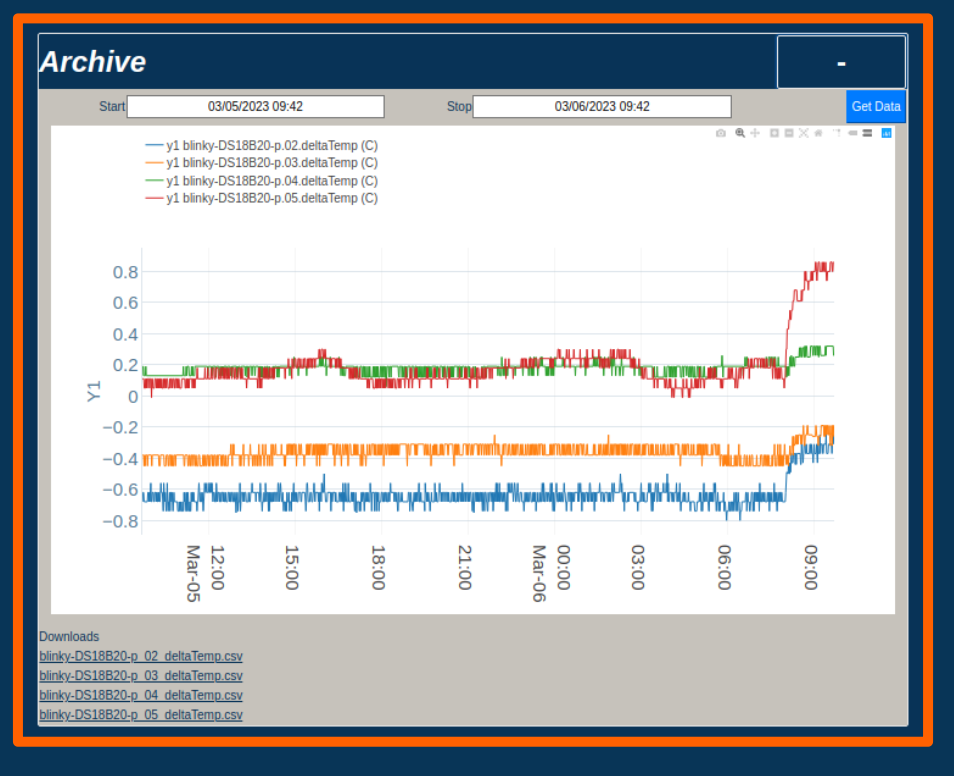
Blinky-Lite Archive Plotter
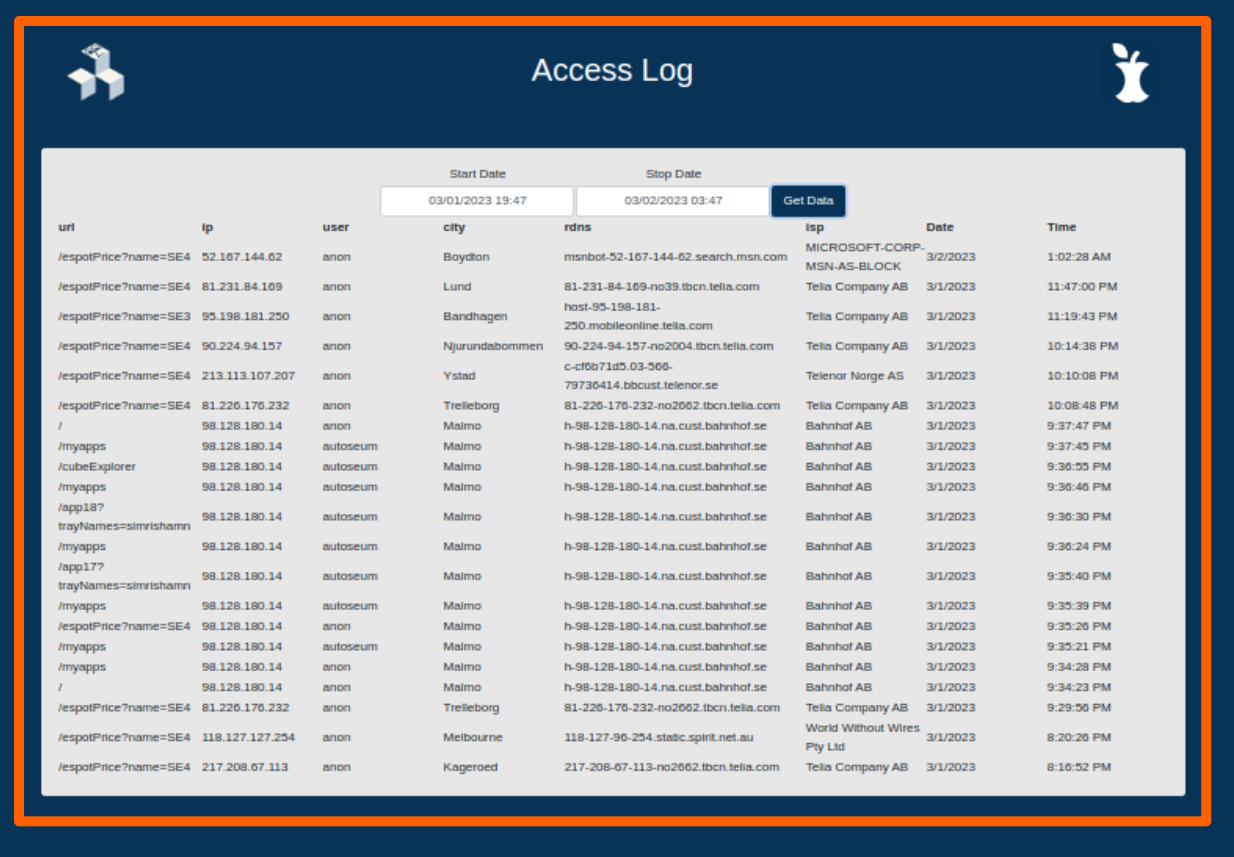
Blinky-Lite Access Log
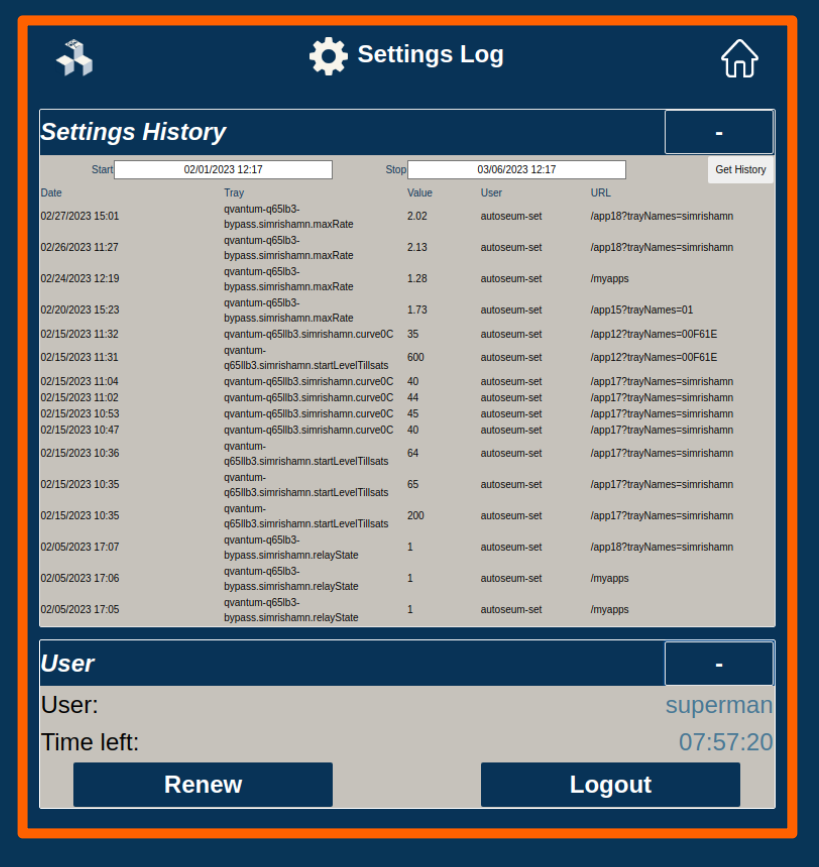
Blinky-Lite Settings Log
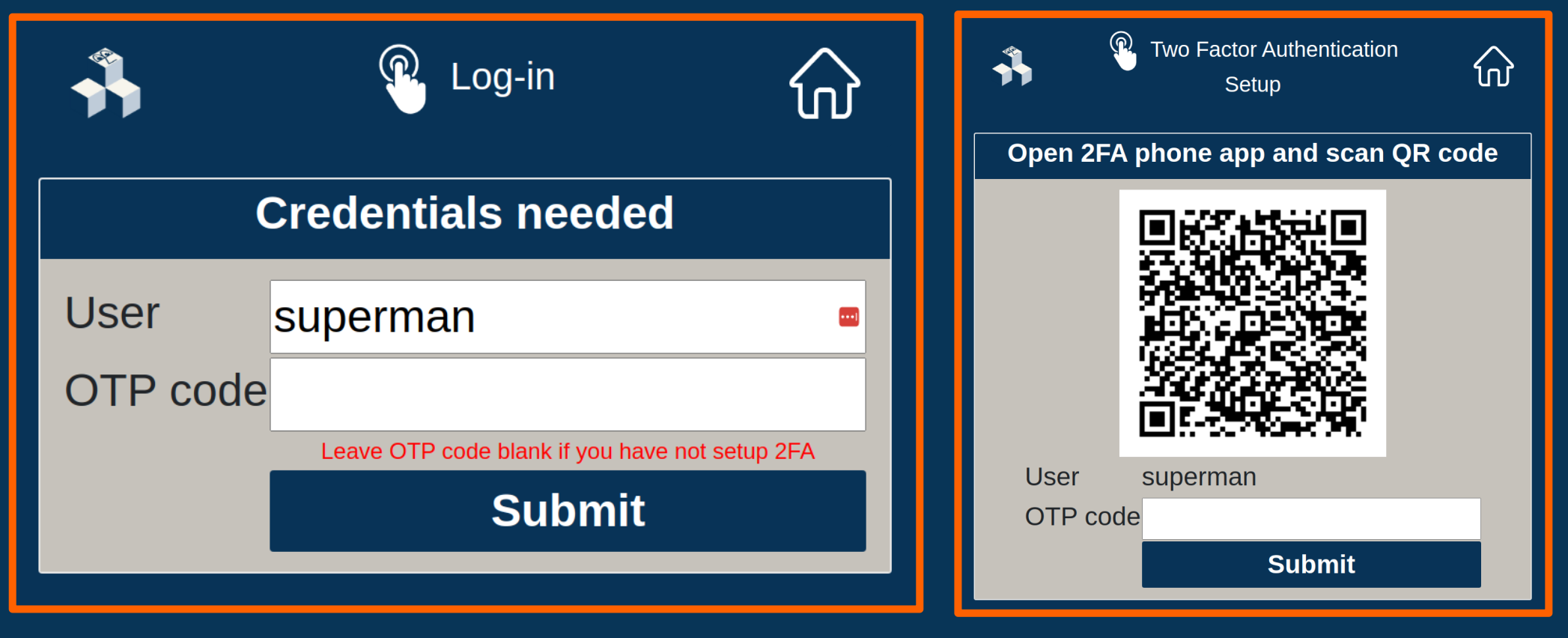
Blinky-Lite Two Factor Authentication
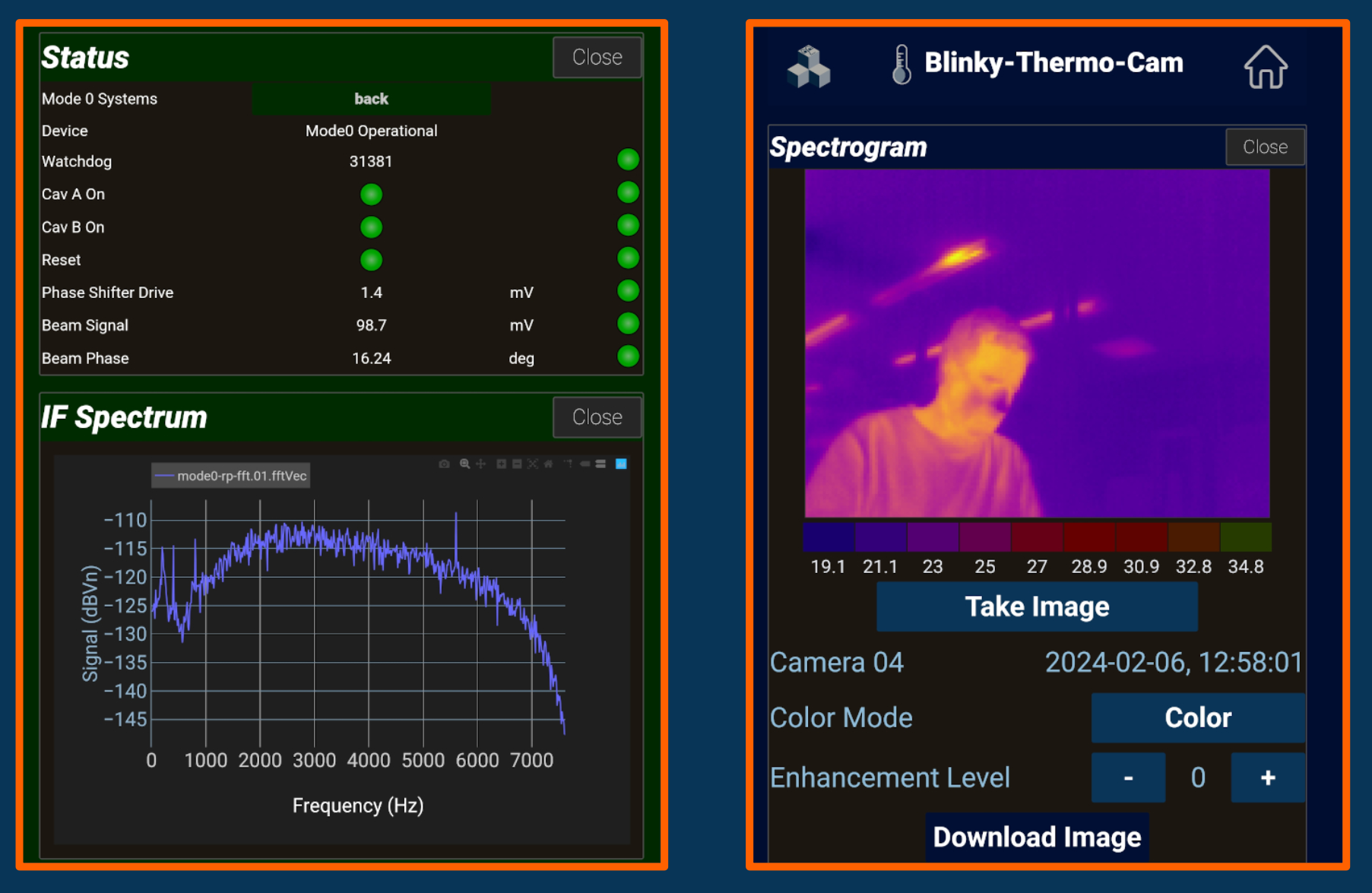
Examples of vector and image data in Blinky-Lite

Blinky-Lite Logbook Application